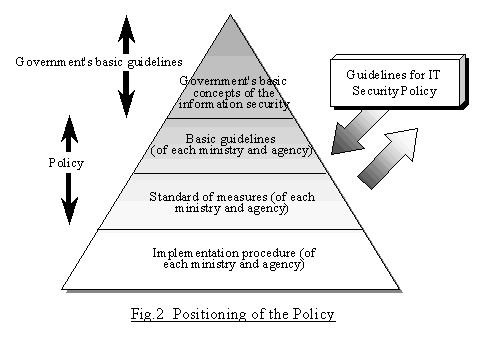
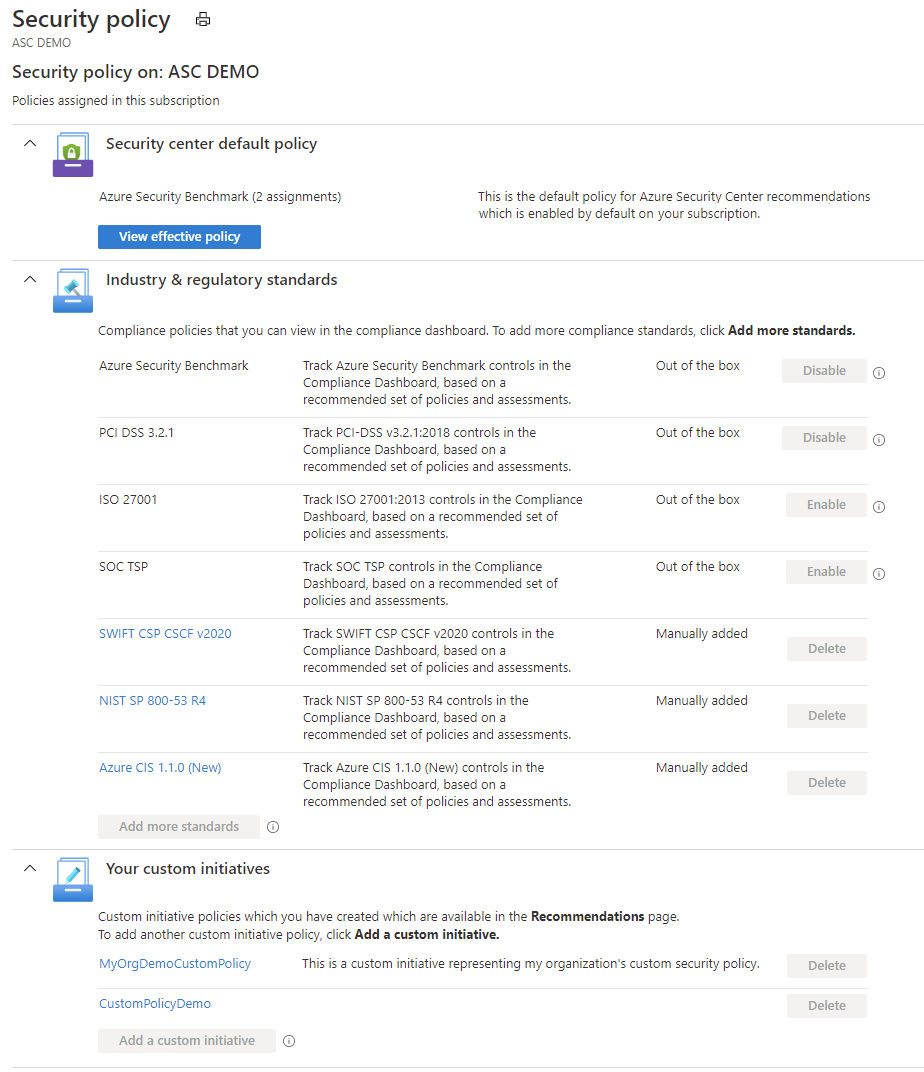
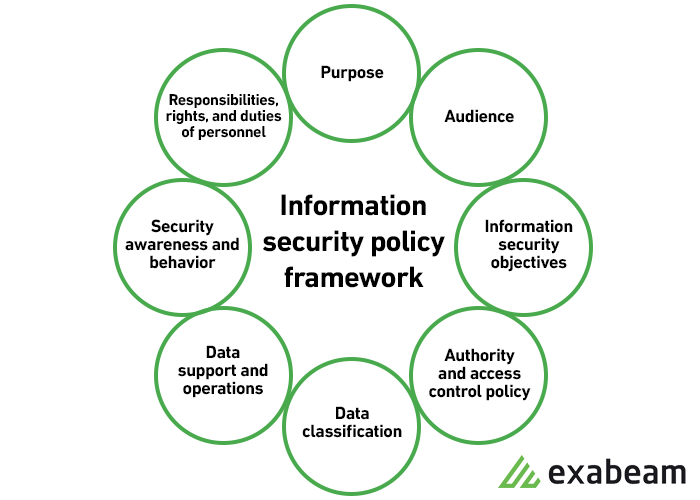
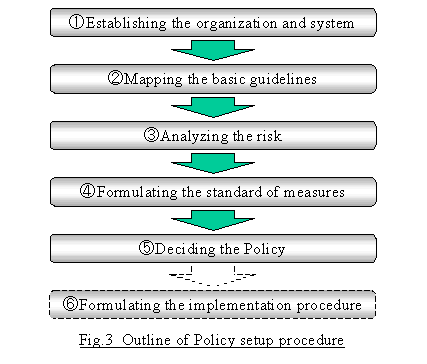
What is Information Security & types of Security policies | Infosavvy Security and IT Management Training

Kubernetes Pod Security Policy 非推奨化にあたり知っておくべきこと #aqua #コンテナ #セキュリティ #kubernetes #k8s #psp #pss - クリエーションライン株式会社
Information Technology Security Policy and Procedures - BIENE IT | Bester Support, sicherste IT, zufriedenste Kunden.

Security Policy In Word Tag Cloud On White Stock Photo, Picture And Royalty Free Image. Image 41230862.